The conversation on the deadlines within encrypted services once again makes the rounds after the reports emerged that the British government was trying to force Apple to open the safeguarding of the encrypted apparatus of icloud ( E2EE). The civil servants would have supported Apple to create a “stolen door” in the service which would allow the actors of the State to access clear data.
The United Kingdom has had sweeping powers to limit the use of solid encryption companies since the transmission of 2016 update to state monitoring powers. According to reports by Washington PostBritish officials used the law on survey powers (IPA) to place the request on Apple – looking for “coverage” access to data that its advanced protection service (ADP) iCloud is designed to protect against third -party access , including Apple himself.
The technical architecture of Apple’s ADP service has been designed in such a way that even the technology giant does not contain encryption keys – thanks to the use of end -to -end (E2EE) – allowing Apple de Apple promise it to “zero knowledge” of the data of its users.
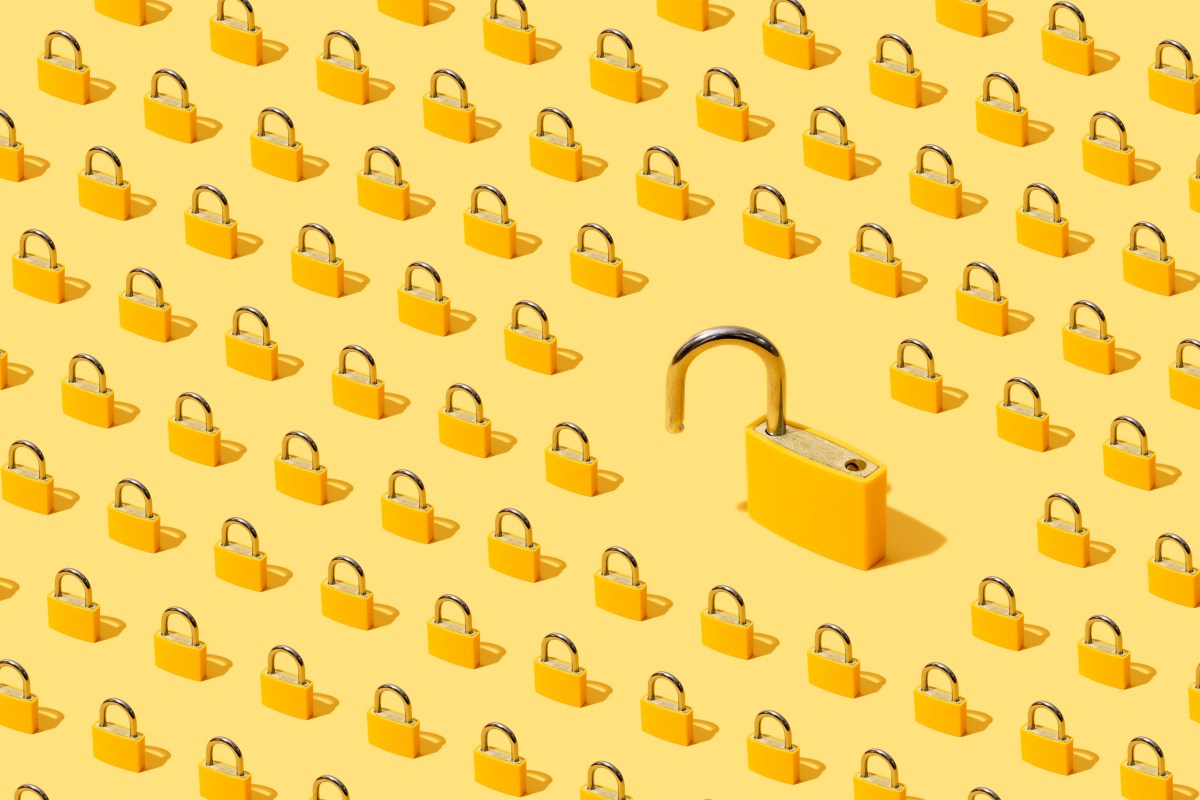
A stolen door is a term generally deployed to describe a secret vulnerability inserted in the code to bypass or undermine security measures in order to activate third parties. In the iCloud case, the order allows British intelligence agents or the police access to the encrypted user data.
While the British government regularly refuses to confirm or deny the reports of the opinions issued under the IPA, security experts have warned that such a secret order could have global ramifications if the iPhone manufacturer is obliged to ‘Weaken the security protections it offers to all users, including those located outside the United Kingdom.
Once a vulnerability in the software, there is a risk that it can be exploited by other types of agents, let’s say hackers and other bad players wishing to access harmful ends – such as identity theft , or acquire and sell sensitive data, or even to deploy ransomware.
This may explain why the predominant phrasing used around attempts focused on the state to access E2EE is this visual abstraction of a stolen door; ask for a vulnerability be intentionally Added to the code makes compromise clearer.
To use an example: with regard to physical doors – in buildings, walls or similar – it is never guaranteed that only the owner or keychain will have exclusive use of this point of entry .
Once an opening exists, it creates an access potential – someone could get a copy of the key, for example, or even force its way by breaking down the door.
The main thing: there is no perfectly selective door that exists to let a particular person pass. If someone can enter, it logically follows that someone else could also use the door.
The same principle of risk of access applies to vulnerabilities added to software (or, in fact, to hardware).
The concept of Nobus (“No one other than us”) Waste has been launched by security services in the past. This specific type of stolen door is generally based on an assessment of their technical capacities to exploit a particular vulnerability above all others – essentially an ostensibly more secure stolen door which can only be accessible by their own agents.
But by nature, prowess and technological capacity are a mobile feat. The evaluation of the technical capacities of other strangers is not an exact science either. The concept “Nobus” is found on already doubtful hypotheses; Any third -party access creates the risk of opening new attack vectors, such as social engineering techniques aimed at targeting the person with “authorized” access.
Unsurprisingly, many security experts reject Nobus as a fundamentally wrong idea. In other words, all access creates risks; Therefore, the push for deadlines is antithetical to solid security.
However, whatever these clear and present security problems, governments continue to put pressure for deadlines. This is why we must continue to talk about it.
The term “stolen door” also implies that these requests can be clandestine rather than public – just as wanderings are not entry points which are public oriented. In the iCloud de Apple case, a compromise request The encryption made under the IPA of the United Kingdom – through a “technical capacity opinion” or the TCN – cannot be legally disclosed by the RECIPIENT. The intention of the law is that such deadlines are secret by design. (The flight of the details of a TCN to the press is a mechanism to bypass an information block, but it is important to note that Apple has not yet made a public comment on these reports.)
According to the rights group, the Electronic border foundationThe term “stolen door” dates back to the 1980s, when the stolen door (and “trapdoor”) was used to refer to secret accounts and / or passwords created to allow someone unknown access to a system. But over the years, the word has been used to label a wide range of attempts to degrade, circumvent or otherwise compromise data security activated by encryption.
Although the wanderings are again in the news, thanks to the United Kingdom after Apple’s iCloud Icloud backups, it is important to know that the data access requirements go back to decades.
In the 1990s, for example, the US National Security Agency (NSA) developed encrypted equipment for the processing of voice messages and data that cooked a stolen door – in order to allow security services to intercept encrypted communications. The “clipper chip”, as it was called, used a key sequestration system – which means that an encryption key was created and stored by government agencies in order to facilitate access to encrypted data in the event where state authorities wanted.
The NSA’s attempt to whisk the tokens with hand doors of the bakery failed in the subject of a lack of adoption following a safety and confidentiality. Although the Clipper chip is credited to have helped to trigger cryptologists to develop and disseminate solid encryption software in order to secure data against the government of the fight against the government.
The Clipper chip is also a good example of how an attempted access to the system has been carried out publicly. It should be noted that deadlines do not always have to be secret. (In the ICLOUD case of the United Kingdom, state agents clearly wanted to access without Apple users knowing it.)
Add to this, governments frequently deploy emotional propaganda around requests to access data in order to stimulate public support and / or put pressure on service providers to comply – for example by arguing that the Access to E2EE is necessary to combat children’s abuse or terrorism or prevent another heinous crime.
The deadlines may however have a way to come back to bite their creators. For example, pirates supported by China were behind the compromise of electronic listening systems mandated by the federal government last fall – apparently having access to data from US of American telecommunications and ISPs thanks to a law 30 -year -old federal who had forced access to the stolen door (although, in this case, non -E2EE data), highlighting the risks of intentionally cooking access points in systems.
Governments must also be concerned about foreign deadlines creating risks for their own citizens and national security.
There have been several cases of Chinese hardware and software suspected of holding deadlines over the years. The concerns concerning the potential risks of a stolen door have led certain countries, including the United Kingdom, to take measures to delete or limit the use of Chinese technological products, such as the components used in critical telecommunications infrastructure, years. The fears of the decline can also be a powerful motivator.